Improving security in ASP.NET MVC using custom headers
This is the first post in a series about ASP.NET security. Looking for security in ASP.NET Core? Check out: The ASP.NET Core security headers guide.

I recently discovered securityheaders.io, produced by the hyper productive Scott Helme. securityheaders.io scans your website and make suggestions to which HTTP response headers to add in order to improve security. I previously used Troy Hunt's ASafaWeb (now closed down), but that one has a slightly different focus and lacks some of the headers.
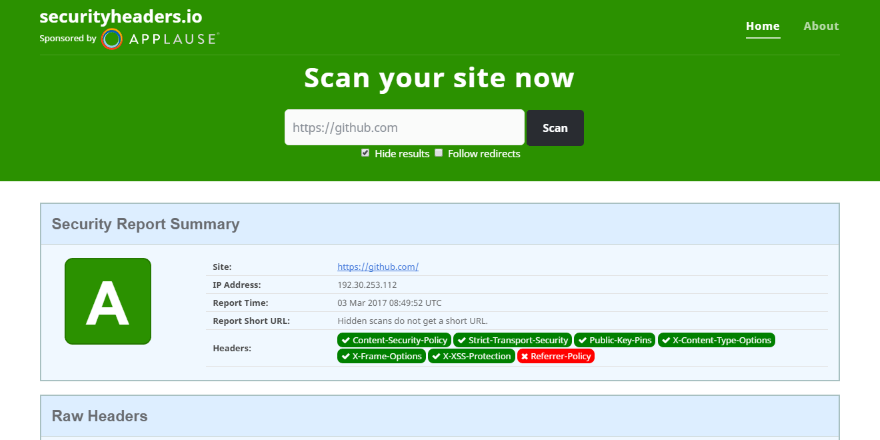
This post is a sum up of not only elmah.io headers added recently, but how to make it more difficult for hackers to compromise your ASP.NET (MVC, Web API, Core) website in general. In the following paragraphs, I have listed a number of HTTP headers that are easily configured and that everyone should implement.
X-Frame-Options
The X-Frame-Options header ensure, that hackers don't iframe your site, in order to trick you into clicking links which you never intended to. If you are using ASP.NET MVC 5 or newer, this header is added automatically. Adding the header in previous versions or other web frameworks is easy using web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Frame-Options" value="DENY" />
</customHeaders>
</httpProtocol>
</system.webServer>
In this example, I deny any possibility of iframing the website. If you are using iframes on the same domain, you can change the value to SAMEORIGIN.
X-Xss-Protection
Since writing this post the
X-Xss-Protectionheader as been deprecated and is no longer recommended.
The X-Xss-Protection is a feature implemented in most modern browser, which will stop loading the page when a cross-site scripting attack is detected. Adding the header happens through web.config as well:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Xss-Protection" value="1; mode=block" />
</customHeaders>
</httpProtocol>
</system.webServer>
The value if 1 simply marks the protection as enabled.
X-Content-Type-Options
To avoid MIME type sniffing, you can add the X-Content-Type-Options header. This makes it harder for hackers to guess the right mime type, by inspecting the content. Adding the header is easily done through web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Content-Type-Options" value="nosniff" />
</customHeaders>
</httpProtocol>
</system.webServer>
Referrer-Policy
Browsers automatically add the Referer header, when a user click a link on your site. This means that a linked website, will be able to see where the users are coming from. While this is a great feature for Analytics, you may have sensitive information in your URLs, which you don't want to forward to other domains. To remove the referrer entirely, add the following header to web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="Referrer-Policy" value="no-referrer" />
</customHeaders>
</httpProtocol>
</system.webServer>
In real life, you may want another value for Referrer-Policy. Removing the referrer entirely, makes it impossible to see the internal traffic flow on your website. Check out Referrer-Policy on mozilla.org for a list of possible values.
X-Permitted-Cross-Domain-Policies
To restrict Flash components to make cross-origin requests, you should disable it entirely (unless you are using Flash of course). To do so, add the X-Permitted-Cross-Domain-Policies to web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Permitted-Cross-Domain-Policies" value="none" />
</customHeaders>
</httpProtocol>
</system.webServer>
Strict-Transport-Security
If you haven't implemented HTTPS on your website, you should. After doing so, you can prevent any communication happening over HTTP using the Strict-Transport-Security header:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="Strict-Transport-Security" value="max-age=31536000; includeSubDomains" />
</customHeaders>
</httpProtocol>
</system.webServer>
The max-age value tells browsers to use this setting for the specified number of seconds. In this case a year. The includeSubDomains part can be excluded, if you are hosting non-HTTPS websites on subdomains (like a blog).
X-Powered-By
The X-Powered-By header is automatically added by ASP.NET. To make it less obvious which technology you are using to host your website, you should remove this header through web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
</customHeaders>
</httpProtocol>
</system.webServer>
X-AspNetMvc-Version
Much like X-Powered-By, X-AspNetMvc-Version is a header automatically added by the framework. To avoid telling hackers that you use MVC and which version, you should remove it. X-AspNetMvc-Version cannot be removed through web.config, but you can disable it from code. Add the following to your Startup.cs or Global.asax.cs:
MvcHandler.DisableMvcResponseHeader = true;
Server
ASP.NET also reveals the server hosting the application. If a hacker know that you are using IIS, this narrows the number of weaknesses that he/she needs to try. To remove the Server header, remove it from code in either a filter or through Global.asax.cs:
protected void Application_PreSendRequestHeaders()
{
if (HttpContext.Current != null)
{
HttpContext.Current.Response.Headers.Remove("Server");
}
}
Permissions-Policy
The Permissions-Policy header (formerly known as Feature-Policy), is a recent addition to the range of security-related headers. When specifying the header, you tell the browser which features your site uses or not. This is a great feature, especially if you embed other websites. To add the header, make the following change in web.config:
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="Permissions-Policy" value="accelerometer=(), camera=(), geolocation=(), gyroscope=(), magnetometer=(), microphone=(), payment=(), usb=()" />
</customHeaders>
</httpProtocol>
</system.webServer>
Here, we tell the browser that our site shouldn't allow use of the accelerometer, camera, and more. Which features you need to add, totally depend on your site. For more information, check out the specification.
Content-Security-Policy
Using the Content-Security-Policy header, requires a bit more explanation. Check out the next post in this series for details: Content-Security-Policy in ASP.NET MVC
elmah.io: Error logging and Uptime Monitoring for your web apps
This blog post is brought to you by elmah.io. elmah.io is error logging, uptime monitoring, deployment tracking, and service heartbeats for your .NET and JavaScript applications. Stop relying on your users to notify you when something is wrong or dig through hundreds of megabytes of log files spread across servers. With elmah.io, we store all of your log messages, notify you through popular channels like email, Slack, and Microsoft Teams, and help you fix errors fast.
See how we can help you monitor your website for crashes Monitor your website
